Cybersecurity Insights
a NIST blog
Digital Identities: Getting to Know the Verifiable Digital Credential Ecosystem
If you are interested in the world of digital identities, you have probably heard some of the buzzwords that have been floating around for a few years now… “verifiable credential,” “digital wallet,” “mobile driver’s license” or “mDL.” These terms, among others, all reference a growing ecosystem around what we are calling “verifiable digital credentials.” But what exactly is a verifiable digital credential? Take any physical credential you use in everyday life – your driver’s license, your medical insurance card, a certification or diploma – and turn it into a digital format stored on your smartphone that can be presented and cryptographically verified either online or in person. That’s a verifiable digital credential (VDC).

Though the concept seems simple, deploying VDCs and understanding their impact on security, privacy and usability in practice can be challenging. If you are looking to implement VDCs for your organization or business, you might find it hard to navigate the terminology, technology, data formats, and protocols that underpin this new and rapidly evolving ecosystem. For this reason, the NIST National Cybersecurity Center of Excellence (NCCoE) is publishing a new blog series to help demystify and highlight some of the standards and technologies that make up the VDC ecosystem. This blog series will leverage the collective expertise of stakeholders from across both government and industry, including partners collaborating with the NCCoE on a project to accelerate the adoption of standards and best practices around VDCs.
In General: The Pieces and Parts of the VDC Ecosystem
Before we jump into the nitty gritty of how the VDC ecosystem works, it’s best we level set on some of the main components and terminology that you might encounter during your exploration into the VDC ecosystem.
Credit:
NIST
| Verifiable Digital Credentials – VDCs are a cryptographically verifiable, digital representation of a credential or attributes secured in a dedicated application, often referred to as a digital wallet. VDCs come in many forms including government credentials (e.g. driver’s licenses), education credentials (e.g. diplomas), proof of coverage such as health insurance, or proof of certain personal characteristics or attributes (e.g. age over 21). VDCs can be presented both online and in-person. For example, you might use a mobile driver’s license on your smartphone to verify your identity with a TSA agent before boarding a plane or present it to a web browser online to verify your identity before opening an account. Fundamentally, VDCs are underpinned by public key cryptography making the credential and the user information it contains cryptographically verifiable. |
|
Credit:
NIST
| Digital Wallet – A digital wallet is a native application on your mobile device – though in the future, may also be stored in the cloud – that holds and secures your VDCs. If you are using an iOS or Android device, you may already have a wallet installed from Apple, Google or Samsung, but additional wallets can also be downloaded from your app store. Depending on the entity issuing the VDC, users may need to download a wallet application supported by the credential issuer before a VDC can be issued to their phone. |
|
Credit:
NIST
| Issuer – The entity issuing the VDC to a user is generally referred to as the “issuer”. This entity provisions the credential and is often the authoritative source that identity proofs the user before credential issuance. The issuer cryptographically signs the VDC so it can be verified when a user presents it to a relying party. |
Credit:
NIST
| Verifier – when a VDC is presented to a website or application, the verifier is responsible for two key steps: first, cryptographically verifying the authenticity and integrity of the credential itself, and second, validating and assessing the specific claims or information contained within the credential. This two-step process ensures both the credential's legitimacy and the relevance and applicability of its contents to the Relying Party's requirements. Before a VDC can be verified, the public key of the issuer must be obtained by the relying party. The verifier may communicate with a trust service to obtain these public keys. Verifiers may also translate VDC claims into other standards-based formats for further consumption by Relying Party applications and identity management system. |
Credit:
NIST
| Trust Service – Trust services may take many forms but in general act as a centralized integration point that enables relying parties to more easily access cryptographic keys generated by issuers. Rather than each relying party communicating with each issuer, trust services may act as a hub and spoke model, allowing replying parties to integrate with a single service and get access to cryptographic keys from multiple issuers. |
Credit:
NIST
| Relying Party – a relying party is an entity that relies upon a verifier’s assertion of a VDC, typically to process a transaction or grant access to information or a system. Examples of relying parties include banks, government agencies, health care institutions and many other entities they may ask you to present your VDC as part of an online or in-person transaction. NOTE: Standards in the VDC ecosystem often talk about Verifiers and Relying Parties interchangeably. In this blog series, we discuss them separately to highlight the distinction between the technical functions that Verifiers provide when processing a VDC and the Relying Party business processes and technologies (including the IDMS) that rely upon the output of the verifier. We find this distinction useful even if in practice the verifier may be run or reside on relying party systems. |
|
Credit:
NIST
| Identity Management System – Identity management system (IDMS) is a general term that refers to software responsible for handling an array of different identity related functions. Account creation, issuance of authenticators, access management and account recovery are just some of the functions that may fall under the IDMS. In the VDC ecosystem, the IDMS is often a back-end service to a web application and might contain the verifier code, integrate with a trust service or handle account actions that would require the user to present their VDC. |
Bringing it all together
Now that we level set on some terminology, let’s talk about how all these pieces and parts come together.
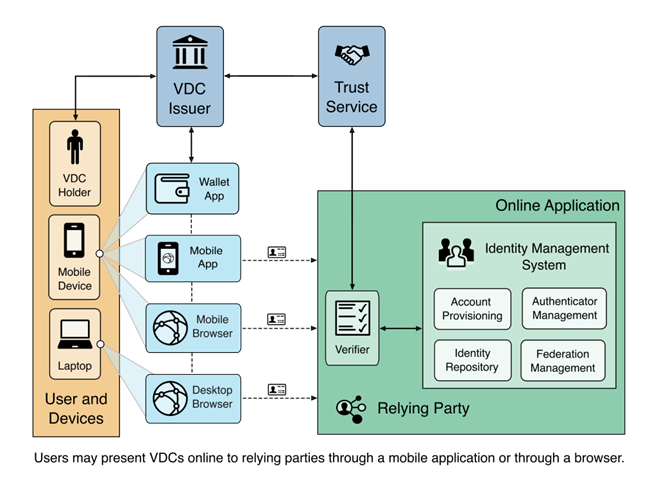
The diagram above is a notional representation of how technologies within the VDC ecosystem might connect and communicate. Now let’s consider an example using mobile driver’s licenses (mDLs) to get a better feel for VDCs in action. mDLs are a type of VDC that act as a digital representation of your physical driver’s license. They are issued by your state DMV and contain the same identity information as your physical license, including your image that’s on file with the DMV. The example below describes how you might use an mDL and highlights which components in the diagram above you may be interacting with.
VDCs in Action
Imagine you are trying to open a bank account online. When you start the online application, the bank prompts you to verify your identity. Instead of visiting a branch, you could choose to use your mobile driver's license (VDC). Since you already have a driver’s license registered with your state, your state DMV (Issuer) can easily issue you an mDL through the wallet app (Digital Wallet) that comes with your mobile operating system. After following the on-screen instructions and completing a selfie match, the wallet application submits a request to your state DMV to have your mDL issued. A few moments later you get an email saying that your mDL is ready for use and has been provisioned to your wallet application.
Returning to the bank’s website, the bank (Relying Party) asks you to present your mDL and shows you a QR code. When you scan the QR, your phone redirects to your wallet app where you perform a biometric authentication and select your new mDL to be presented to the bank’s website. Using a central service (Trust Service) the banking website has already downloaded public keys for valid mDLs issued by your DMV. When you present your mDL to the banking website, it cryptographically verifies (Verifier) your mDL without “phoning home” to the DMV or letting the DMV know your mDL was used to create an account with the bank. Through a secure connection, your identity information contained in the mDL is provided to the banking website. The bank now has sufficient information to confirm your identity and you are now allowed to create your financial account (IDMS).
Though you completed this process by visiting the bank’s website on a desktop browser, you could have just as easily used a mobile browser or downloaded and used your bank’s mobile app.
But Wait! There’s more!
The above scenario elucidates what VDCs look like on the surface, but underneath the hood, there are several protocols, data formats and design patterns that are currently evolving within standards bodies around the world. In our future blog posts, we’ll break down the various elements of the VDC ecosystem to highlight where this work is happening, the different standards that are being developed, which parts of the ecosystem those standards address and the opportunities and open challenges that still exist within the VDC ecosystem.
If you'd like to be notified when our blog posts go live, consider visiting our webpage and joining our community of interest to get regular updates on NCCoE’s work.


