Cybersecurity Insights
a NIST blog
Next Up: Integrating Information and Communication Technology Risk Programs with Enterprise Risk Management

Given the increasing reliance of organizations on technologies over the past 50 years, a number of risk disciplines have evolved into full-fledged risk programs. In recent years, cybersecurity, supply chain, and privacy risk management programs have formalized best practices. Yet the rapid evolution of these disciplines sometimes has led to miscommunication and inefficiencies between those risk programs and overarching enterprise risk management (ERM) portfolio. The years ahead will focus on optimizing coordination and communication between all risk programs and ERM.
To be supportive of mission and business objectives, each risk program must understand how they support the ERM portfolio. An ERM context aggregates and normalizes organizations’ risks into risk registers and policies. This enables government and critical infrastructure entities to quantify consequences and allocate resources commensurate with enterprise exposure and shareholder/stakeholder value. As enterprise consequences are quantified in financial, mission and reputation metrics, similar to those attributed to other enterprise risks, they enable executives and public officials to prudently reallocate resources among all their particular competing risk types.
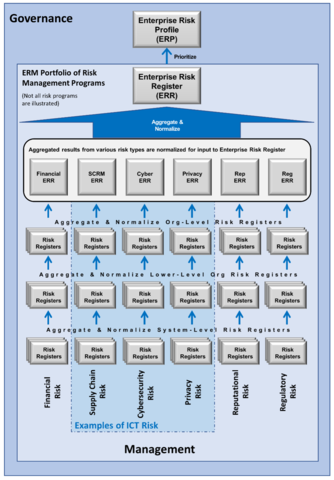
In recent years, the NIST Information Technology Laboratory (ITL) has been publishing guidance to codify risk management best practices for individual programs such as privacy, supply chain, and cybersecurity. In acknowledgement of its expansive charter and emerging technologies, ITL is broadening its risk guidance to include how all information and communication technology (ICT) risk programs integrate into ERM. This activity explains how frameworks like the Cybersecurity Framework, Privacy Framework, artificial intelligence, information systems and organizations and Cyber Supply Chain Risk Management will work together to support ERM. Each of these ICT frameworks is representative of a risk program. Risks within, across, and in-between those programs form a mosaic of peer and interrelated ICT risks.
ICT risk must address myriad of enterprise computing platforms and signals. These include numerous digital technologies that create, modify, process, communicate and control information as well as the application technologies. This system-of-systems provides or assists enterprise or personal endeavors and the resultant data represents information, control signals and sensor readings. As with other complex systems-of-systems, the interconnectedness of these technologies produces system behaviors which cannot be determined by the behavior of its individual components. That interconnectedness causes risks that exist between risk programs and across multiple risk programs. ITL is proceeding with a more interconnected approach to risk frameworks and programs to address this special subsect of risks.
In the contemporary enterprise, emergency and real-time circumstances can turn a relatively minor ICT-based risk into true Operational Risks that disrupt an organization’s ability to perform mission or business functions. The upcoming ICT risk management guidance will address some of these challenges, including the notion that real-time systems bring real-time risks and need real-time resilience.
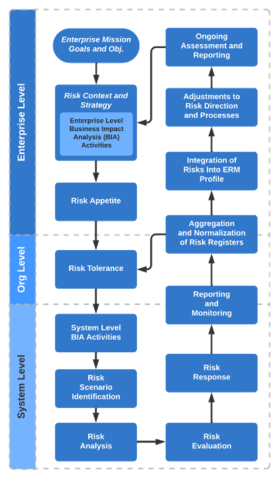
A recent NIST Interagency Report pioneers a use case of ERM integration. The NIST IR 8286 Series of publications demonstrates how to better integrate cybersecurity with ERM. The Series helps government and critical infrastructure entities effectively quantify, finance, and drive their cybersecurity programs commensurate with enterprise exposure, as well as shareholder and stakeholder value. The Series acknowledges the need for ongoing bidirectional communication between ERM and risk programs recognizing that the risk disciplines both inform and receive direction from ERM. Specifically, the communication of risk appetite statements from the ERM portfolio is a way for risk programs to better identify and monitor risks using a variety of related methods such as risk tolerance statements, key performance indicators, key risk indicators, and controls. Similarly, the NISTIR formalizes the use of risk registers to communicate risks and risk responses between program and portfolio levels. The series highlights industry best practices for coordination by elevating risks within an organization for oversight and escalating risks within an organization for higher level ownership.
In the upcoming months, NIST will finalize key publications within the NIST IR 8286 Series and publish guidance on how to better integrate ICT risk programs into ERM. These publications will focus on better communication and coordination across risk programs and portfolio. Please continue providing feedback on these important guidelines, so we can all enjoy a more effective and efficient future for risk management.


