Cybersecurity Framework 1.1 Components
The Introduction to the Components of the Framework page presents readers with an overview of the main components of the Framework for Improving Critical Infrastructure Cybersecurity ("The Framework") and provides the foundational knowledge needed to understand the additional Framework online learning pages. If you're already familiar with the Framework components and want to learn more about how industry is using the Framework, see Uses and Benefits of the Framework.
Framework Components
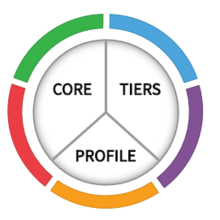
The Cybersecurity Framework consists of three main components:
Framework Core
The Core is a set of desired cybersecurity activities and outcomes organized into Categories and aligned to Informative References. The Framework Core is designed to be intuitive and to act as a translation layer to enable communication between multi-disciplinary teams by using simplistic and non-technical language. The Core consists of three parts: Functions, Categories, and Subcategories. The Core includes five high level functions: Identify, Protect, Detect, Respond, and Recover. These 5 functions are not only applicable to cybersecurity risk management, but also to risk management at large. The next level down is the 23 Categories that are split across the five Functions. The image below depicts the Framework Core's Functions and Categories.
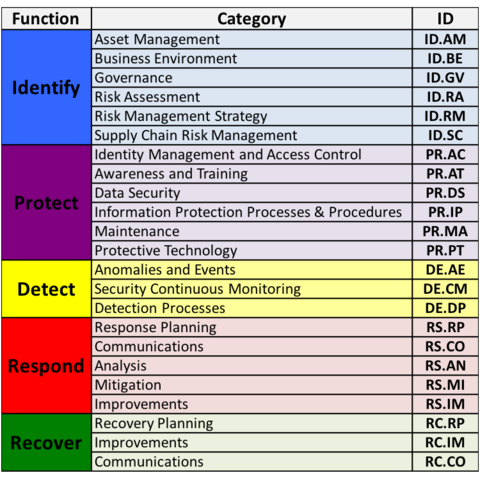
The Categories were designed to cover the breadth of cybersecurity objectives for an organization, while not being overly detailed. It covers topics across cyber, physical, and personnel, with a focus on business outcomes.
Subcategories are the deepest level of abstraction in the Core. There are 108 Subcategories, which are outcome-driven statements that provide considerations for creating or improving a cybersecurity program. Because the Framework is outcome driven and does not mandate how an organization must achieve those outcomes, it enables risk-based implementations that are customized to the organization's needs.
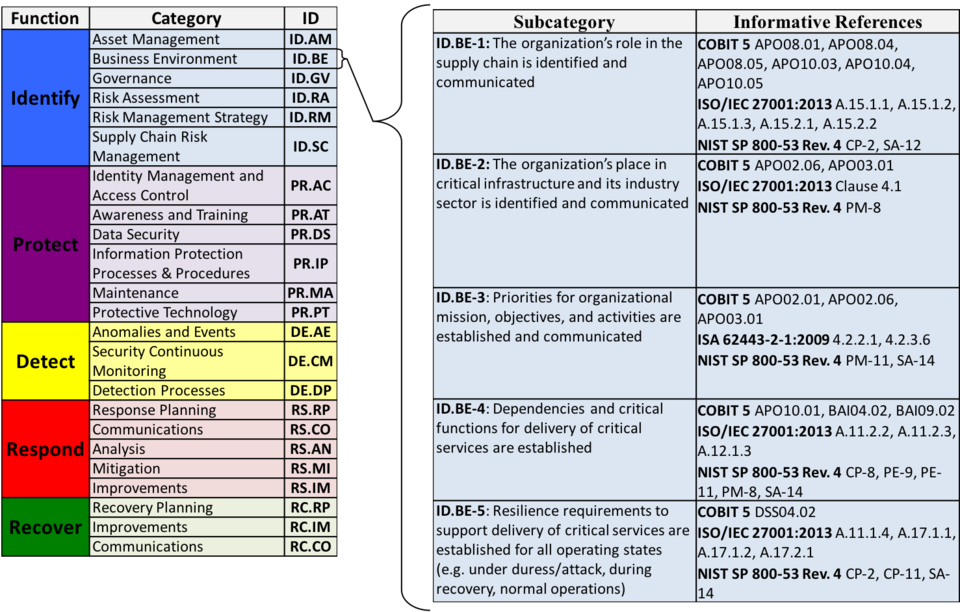
The five Subcategories pictured from the Business Environment Category (ID.BE) provide an example of the outcome focused statements that are found throughout the core. The column to the right, Informative References support the Core by providing broad references that are more technical than the Framework itself. Organizations may wish to use some, none, or all of these references to inform the activities to undertake to achieve the outcome described in the Subcategory.
For more information regarding the Informative References, see the Informative References Learning Module.
Framework Implementation Tiers
Tiers describe the degree to which an organization’s cybersecurity risk management practices exhibit the characteristics defined in the Framework. The Tiers range from Partial (Tier 1) to Adaptive (Tier 4) and describe an increasing degree of rigor, and how well integrated cybersecurity risk decisions are into broader risk decisions, and the degree to which the organization shares and receives cybersecurity info from external parties.

Tiers do not necessarily represent maturity levels. Organizations should determine the desired Tier, ensuring that the selected level meets organizational goals, reduces cybersecurity risk to levels acceptable to the organization, and is feasible to implement, fiscally and otherwise.
Framework Profiles
Profiles are an organization's unique alignment of their organizational requirements and objectives, risk appetite, and resources against the desired outcomes of the Framework Core. Profiles can be used to identify opportunities for improving cybersecurity posture by comparing a “Current” Profile with a “Target” Profile.

Profiles are about optimizing the Cybersecurity Framework to best serve the organization. The Framework is voluntary, so there is no ‘right’ or ‘wrong’ way to do it. One way of approaching profiles is for an organization to map their cybersecurity requirements, mission objectives, and operating methodologies, along with current practices against the subcategories of the Framework Core to create a Current-State Profile. These requirements and objectives can be compared against the current operating state of the organization to gain an understanding of the gaps between the two.
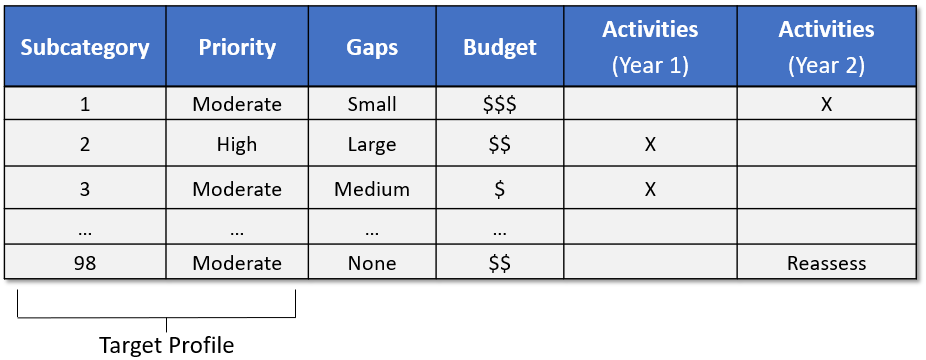
The creation of these profiles, and the gap analysis allows organizations to create a prioritized implementation plan. The priority, size of gap, and estimated cost of the corrective actions help organizations plan and budget for cybersecurity improvement activities.
For an expanded explanation of the Framework components or the Framework implementation process, see the 7 steps in the Framework Document. Also, for examples of Framework Profiles, please review the following Resources.
Additional Resources
Components of Cybersecurity Framework Presentation (PPTX | 2.1 MB)

