Using Privacy Framework 1.1
Informative References support Privacy Framework 1.1 use by mapping to the Privacy Framework Core. Informative References include crosswalks, Profiles, guidelines, and tools. Informative References can be sector, law, or technology-specific. While NIST produces some Informative References, any organization or industry sector can develop these mappings as technology and related business needs evolve. By relying on consensus-based standards, guidelines, and practices, the tools and methods available to achieve positive privacy outcomes can support technological innovation and scale across borders to accommodate the global nature of privacy risks.
Crosswalks that map the provisions of standards, laws, and regulations to the Privacy Framework Core can help organizations determine which activities or outcomes to prioritize to meet obligations such as regulatory requirements. The Privacy Framework online Resource Repository contains a variety of crosswalks to support Privacy Framework use.
An Organizational Profile is a selection of specific Functions, Categories, and Subcategories from the Privacy Framework 1.1 Core to represent an organization’s current privacy activities (Current Profile) or desired outcomes (Target Profile). A Community Profile addresses shared interests and goals among a group of organizations and can be developed for a particular sector, subsector, technology, or other use case. Organizations can use Community Profiles as Informative References upon which to base their own Organizational Profiles.
Profiles help organizations and communities understand, tailor, assess, prioritize, and communicate the Framework Core’s outcomes by considering operational context, mission objectives, stakeholder expectations, threat landscape, and requirements. Profiles are useful tools for strategic planning and collaboration, including prioritizing actions to achieve specific outcomes in the Core and communicating with stakeholders.
The Privacy Framework online Resource Repository contains Profiles to support Privacy Framework 1.1 use. The National Cybersecurity Center of Excellence (NCCoE) also offers online resources to support organizations seeking to utilize existing Community Profiles or to develop their own Community Profile(s). Learn more here.
Organizations can utilize guidelines and tools mapped to Privacy Framework 1.1 Core Functions, Categories, and Subcategories to gather information, techniques, or other references to support achievement of privacy risk management outcomes and activities. Examples of guidelines and tools include:
- NIST Special Publications
- NIST Internal Reports
- Open-source tools
The Privacy Framework online Resource Repository contains a mapping between Privacy Framework 1.1 Subcategories and relevant guidelines and tools. Risk assessment and disassociability tools can also be found in the Privacy Engineering Program Collaboration Space.
Gaps in mappings to Informative References can help identify where additional or revised standards, guidelines, and practices are needed. An organization that discovers insufficient Informative References for a given Core Subcategory might collaborate with technology leaders and standards bodies to draft, develop, and coordinate new standards, guidelines, or practices to address emerging needs.
Organizations can find a repository of Informative References at the NIST Privacy Framework website (https://www.nist.gov/privacy-framework). The NIST Cybersecurity and Privacy Reference Tool enables stakeholders to interactively browse and export reference data from NIST publications, including the Privacy Framework, in a structured format that is human- and machine-consumable. NIST also helps subject matter experts define standardized online informative references between elements of cybersecurity, privacy, and workforce documents like the Privacy Framework through the National Online Informative Reference (OLIR) Program.
Accountability can be expressed as a cultural value, as governance policies and procedures, or as traceability relationships between privacy requirements and controls. Privacy risk management using Privacy Framework 1.1 supports accountability throughout an organization by connecting senior executives, business/process managers, and implementation/operations personnel. This facilitates the development and implementation of governance policies and procedures that align with organizational privacy values and risk tolerance, ensuring that privacy requirements and responsibilities are clearly communicated and understood at all levels. Personnel at the implementation/operations level also select, implement, and assess controls as the technical and policy measures that meet the privacy requirements; they report on progress, gaps, incident management, and changing privacy risks so organizational decision-makers can better understand and respond appropriately.
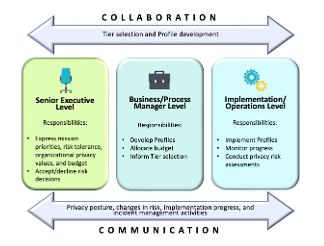
The Figure above describes the bi-directional collaboration and communication flows within an organization and how elements of Privacy Framework 1.1 can be incorporated to facilitate the process. In this way, organizations can use the Privacy Framework as a tool to support accountability. They can also use the Privacy Framework in conjunction with other frameworks and guidance that provide additional practices to achieve accountability within and between organizations.
Using a simple model of “Ready, Set, Go” phases, Privacy Framework 1.1 can help organizations establish a new privacy program or improve an existing program. Organizations can use the Identify-P and Govern-P Functions to get “ready" by identifying their data processing activities, privacy risks, privacy values, and legal requirements. Organizations can then “set” an action plan based on the differences between their Current and Target Profiles and implement the action plan to “go” towards the achievement of desired privacy outcomes.
In the "Ready" phase, an organization should use the Identify-P and Govern-P Functions to understand its mission or business environment, establish organizational privacy values and policies, determine risk tolerance, and conduct privacy risk assessments. This provides a foundation for developing Current and Target Profiles.
In the "Set" phase, an organization completes its Current Profile by determining which Privacy Framework 1.1 Category and Subcategory outcomes are being achieved. Noting if an outcome is partially achieved will help support subsequent steps. Informed by the results of the “Ready” phase, the organization then develops a Target Profile focused on the assessment of the Categories and Subcategories describing its desired privacy outcomes. The organization identifies gaps between the Current and Target Profiles and creates a prioritized action plan to address these gaps.
In the "Go" phase, an organization prioritizes actions to address gaps identified in the "Set" phase and adjusts its current privacy practices to achieve the Target Profile. This phase involves continuous assessment and improvement of the privacy posture, monitoring progress, and updating Profiles to adapt to changing risks and business objectives.
The Privacy Framework can be aligned with the SDLC by integrating the Target Profile with the SDLC phases: plan, design, build/buy, deploy, operate, and decommission. This helps privacy outcomes to be prioritized and transformed into privacy capabilities and requirements throughout the system's life cycle.
In the plan phase, the Target Profile helps transform prioritized privacy outcomes into privacy capabilities and requirements for the system. This enables privacy considerations to be integrated from the beginning of the system development process.
During the design phase, the Target Profile is used to validate that the privacy capabilities and requirements match the organization's needs and risk tolerance. This enables the system design to be aligned with the desired privacy outcomes.
In the deploy phase, the Target Profile serves as an internal list to verify that all privacy capabilities and requirements have been implemented. This helps the system meet the established privacy outcomes before it becomes operational.
Privacy outcomes determined by using the Privacy Framework should serve as a basis for ongoing operation of the system. This includes occasional reassessment, capturing results in a Current Profile, to verify that privacy capabilities and requirements are still fulfilled. Privacy risk assessments typically focus on the data life cycle. Aligning the system development life cycle and the data life cycle helps organizations to better manage privacy risks and informs the selection and implementation of privacy controls to meet privacy requirements.
The data processing ecosystem encompasses the complex and interconnected relationships among entities involved in creating or deploying systems, products, or services or any components that process data within an organization.
An organization's role in the data processing ecosystem affects its legal obligations and the measures it may take to manage privacy risk. Understanding these roles helps in identifying and managing privacy risks effectively.
Profiles can be developed to manage privacy risk by expressing privacy requirements to external service providers, demonstrating measures adopted to process data in line with contractual obligations, and establishing common Profiles for industry sectors. This helps in aligning privacy risk management priorities across different entities.
Examples include:
- An organization that makes decisions about how to collect and use data about individuals may use a Profile to express privacy requirements to an external service provider (e.g., a cloud provider to which it is exporting data); the external service provider that processes the data may use its Profile to demonstrate the measures it has adopted to process data in line with contractual obligations.
- An organization may express its privacy posture through a Current Profile to report results or to compare with acquisition requirements.
- An industry sector may establish a common Profile that can be used by its members to customize their own Profiles.
- A manufacturer may use a Target Profile to determine the capabilities to build into its products so that its business customers can meet the privacy needs of their end users.
- A developer may use a Target Profile to consider how to design an application that enables privacy protections when used within other organizations’ system environments.
The Privacy Framework provides a common language to communicate privacy requirements, which is particularly notable when the data processing ecosystem crosses national boundaries.
Organizational practices that support communication may include:
- Determining privacy requirements;
- Enacting privacy requirements through formal agreement (e.g., contracts, multi-party frameworks);
- Communicating how those privacy requirements will be verified and validated;
- Verifying that privacy requirements are met through a variety of assessment methodologies; and
- Governing and managing the above activities.
Profiles can help organizations make decisions about buying products and services by:
- Generating Prioritized Privacy Requirements: Organizations can use Current or Target Profiles to create a prioritized list of privacy requirements that align with their privacy goals.
- Evaluating Partners: Profiles allow organizations to evaluate partners’ systems, products, or services against the specified privacy outcomes.
- Making Informed Trade-Offs: When it’s not possible to impose a set of privacy requirements on a supplier, organizations can use the Profiles to make the best buying decision among multiple suppliers, considering known gaps and residual risks.
- Mitigating Residual Risks: If the purchased system, product, or service does not meet all the objectives described in the Profile, organizations can address the residual risk through mitigation measures or other management actions.
This approach allows for buying decisions to be aligned with the organization’s privacy objectives and risk management strategies.
Questions?
If you have any questions, email privacyframework [at] nist.gov (privacyframework[at]nist[dot]gov).

