Next Generation Access Control System and Process for Controlling Database Access
Patent Number: 10,127,393
Problem
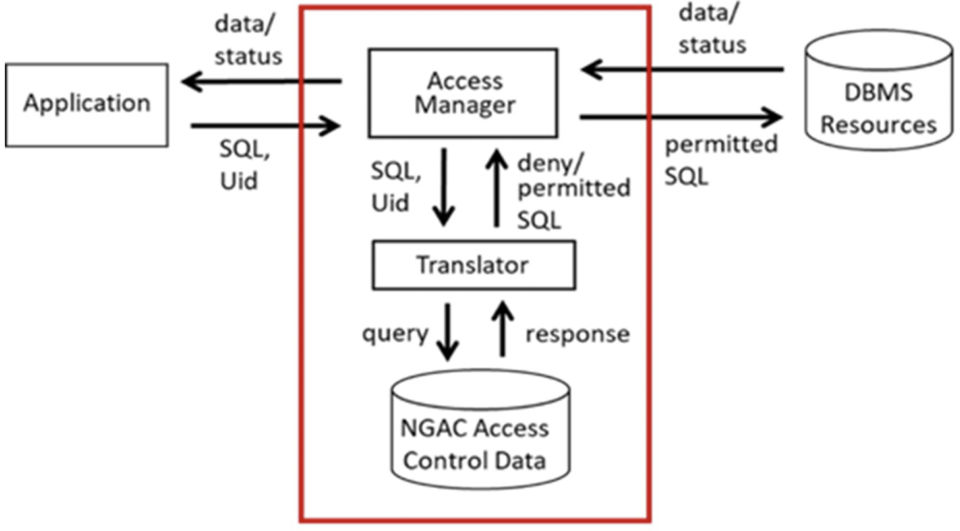
Given the sensitivity of much of the data that resides in DBMSs, controlled access in accordance with policy is a fundamental requirement. While policymakers have specified a wide variety of access controls to address real-world security issues, only a small subset of these policies can be enforced in database scenarios. Furthermore, today’s approach to access control is by no means standardized, requiring separate configurations of an often-complicated amalgamation of mechanisms, including those that are custom-implemented in applications and specific to DBMS products.
Invention
Provides a universal access control layer between applications and DBMSs, following a standardized ABAC model (NGAC*) that is a) DBMS-agnostic, b) does not require modification of the DBMS software, and c) can enforce types of access policies and at a granularity not typically available in database scenarios with a minimal performance impact. Operationally, users issue untrusted queries, and NDAC only allows authorized queries to be sent to the database.
*Next-Generation Access Control (NGAC) is an ANSI/INCIT standard.
Potential Commercial Applications
- Prevents data breaches: Provides a simplified and standardized means of protecting databases from queries sent from any application.
- Improves data usage: Users issue broad sweeping queries, and NDAC allows access to an optimal set of permissible data per enterprise policies.
- Cost savings: Developers no longer need to implement access control at the software level, which significantly saves time and reduces organizational costs.
- Uniform policy enforcement: Enforces common policy over queries sent to multiple databases.
Competitive Advantage
- Before the fact audit: Can determine DBMS resources (i.e., rows, columns, tables, and fields) that a user is authorized to access in advance of the user issuing a query. It can be used to demonstrate adherence to security and privacy policies.
- One mechanism: In contrast to other middleware approaches, NDAC does not manage and coordinate multiple access control mechanisms to achieve fine-grained access control. That is, it provides cell-level protection without resorting to data masking.
- Performance: linear-time algorithms for translating user queries to permitted queries.

