Getting Started
In this animated story, privacy experts explain how the Privacy Framework can be used to build trust in their products and services, better communicate their privacy practices, and help meet their compliance obligations.
Statistics in the video were taken from Pew Research Center, November 2019, “Americans and Privacy: Concerned, Confused and Feeling Lack of Control Over Their Personal Information.”
Overview and Privacy Risk Management Approach
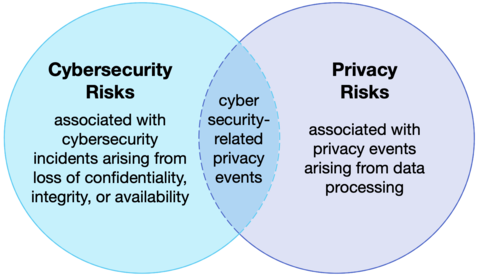
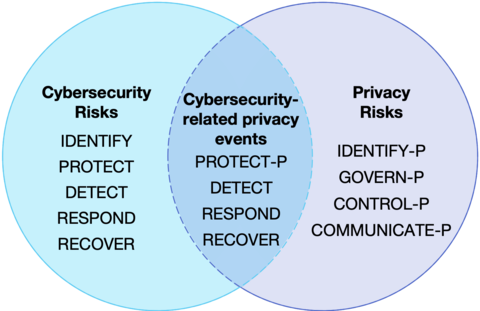
Managing cybersecurity risk contributes to managing privacy risk, but is not sufficient, as privacy risks can also arise by means unrelated to cybersecurity incidents, as illustrated by the Venn diagram. Having a general understanding of the different origins of cybersecurity and privacy risks is important for determining the most effective solutions to address the risks.
The Privacy Framework is a voluntary tool intended to help organizations identify and manage privacy risk to build innovative products and services while protecting individuals’ privacy. The Privacy Framework approach to privacy risk is to consider privacy events as potential problems individuals could experience arising from system, product, or service operations with data, whether in digital or non-digital form, through a complete life cycle from data collection through disposal.
These data operations are described in the singular as a data action and collectively as data processing. The problems individuals, whether singly or in groups (including at a societal level), can experience as a result of data processing can be expressed in various ways, but NIST describes them as ranging from dignity-type effects such as embarrassment or stigmas to more tangible harms such as discrimination, economic loss, or physical harm.
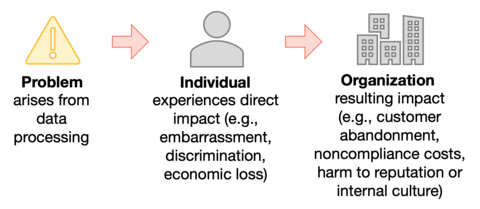
As a result of the problems individuals experience, an organization may experience impacts such as noncompliance costs, revenue loss arising from customer abandonment of products and services, or harm to its external brand reputation or internal culture. Organizations commonly manage these types of impacts at the enterprise risk management level; by connecting problems that individuals experience to these well-understood organizational impacts, organizations can bring privacy risk into parity with other risks they are managing in their broader portfolio and drive more informed decision-making about resource allocation to strengthen privacy programs.
For more about this approach to privacy risk management, see Section 1 of the Framework.
Framework Structure
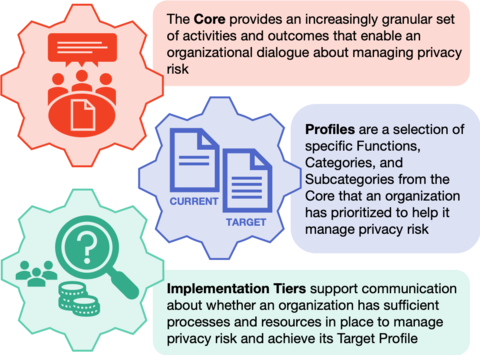
Modeled after the Framework for Improving Critical Infrastructure Cybersecurity (Cybersecurity Framework), the Privacy Framework is composed of three parts: Core, Profiles, and Implementation Tiers.
The Core is a set of privacy protection activities and outcomes that allows for communicating prioritized privacy protection activities and outcomes across an organization from the executive level to the implementation/operations level. The Core is further divided into key Categories and Subcategories—which are discrete outcomes—for each of the five Functions, Identify-P, Govern-P, Control-P, Communicate-P, and Protect-P.
Profiles represent an organization’s current privacy activities or desired outcomes. To develop a Profile, an organization can review all of the outcomes and activities in the Core to determine which are most important to focus on based on business or mission drivers, data processing ecosystem role(s), types of data processing, and individuals’ privacy needs. The Core is not a checklist of actions to perform; an organization selects the privacy protection activities and outcomes consistent with its risk strategy to protect individuals’ privacy.
Implementation Tiers provide a point of reference on how an organization views privacy risk and whether it has sufficient processes and resources in place to manage that risk. Tiers reflect a progression from informal, reactive responses to approaches that are agile and risk informed.
Complementary Frameworks
The Privacy Framework and Cybersecurity Framework can be used together to address different aspects of cybersecurity and privacy risks. Identify-P, Govern-P, Control-P, Communicate-P, and Protect-P can be used to manage privacy risks arising from data processing. Protect-P is specifically focused on managing risks associated with cybersecurity-related privacy events (e.g., privacy breaches). The Cybersecurity Framework, although intended to cover all types of cybersecurity incidents, can be leveraged to further support the management of risks associated with cybersecurity-related privacy events by using the Detect, Respond, and Recover Functions. Alternatively, organizations may use all five of the Cybersecurity Framework Functions in conjunction with Identify-P, Govern-P, Control-P, and Communicate-P to collectively address privacy and cybersecurity risks. This figure uses the Venn diagram from above to demonstrate how the Functions from both frameworks can be used in varying combinations to manage different aspects of privacy and cybersecurity risks.
For more about this structure, see Section 2 of the Framework.
Using the Framework
The Framework can help organizations answer the fundamental question, “How are we considering the privacy impacts to individuals as we develop our systems, products, and services?” To account for an organization's unique needs, use of the Framework is flexible, although it is designed to complement existing business and system development operations. For example, an organization may already have robust privacy risk management processes, but may use the Core’s five Functions as a streamlined way to analyze and articulate any gaps. Alternatively, an organization seeking to establish a privacy program can use the Core’s Categories and Subcategories as a reference.
There are a variety of ways to use the Framework, including to:
- manage privacy risk among different organizational roles in the data processing ecosystem;
- establish or improve a privacy program using a Ready, Set, Go model; and,
- to strengthen organizational accountability through collaboration and communication.
For more about some of the ways it can be used, see Section 3 of the Framework.