Blogrige
The Official Baldrige Blog


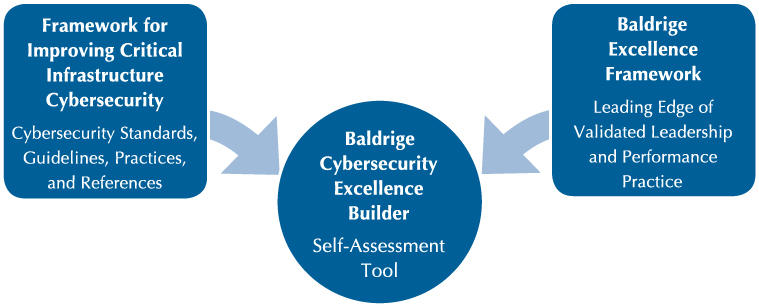
Building a cybersmart organization in today’s fast-moving digital world requires a framework and system for benchmarking security efforts. Consider using the free Baldrige Cybersecurity Excellence Builder (BCEB), a self-assessment tool that blends organizational assessment approaches from the Baldrige Excellence Framework® with the concepts and principles of NIST's Cybersecurity Framework. The BCEB’s goals are to
- help organizations understand the robustness and effectiveness of cybersecurity programs and practices,
- help organizations gauge how cybersecurity efforts align to organizational strategy,
- emphasize tracking and use of performance metrics to drive decision making,
- spread effective use of NIST’s Cybersecurity Framework, and
- support the Baldrige Performance Excellence Program’s purpose of improving organizations’ performance and sustainability/competitiveness.
How the BCEB Helps Leaders and Managers
The BCEB is intended for use by leaders and managers who are concerned with and responsible for an organization’s mission-driven, cybersecurity-related policy and operations. It is most valuable as a voluntary self-assessment of an entire organization’s cybersecurity risk management program; it is also useful in assessing a subunit, multiple subunits, or parts of an organization. Ideally, suppliers and partners also should use the BCEB since they can have immediate and extensive impacts on cybersecurity risks.
The BCEB guides users toward a better understanding of the effectiveness of cybersecurity risk-management efforts and identifies improvement opportunities in the context of their overall organizational performance while illuminating key information about
- organizational and cybersecurity leaders,
- cybersecurity in the context of the organization’s overall strategy,
- cybersecurity needs and expectations of internal and external customers,
- measurement of cybersecurity performance in the context of overall performance measurement,
- the overall workforce and the workforce with special cybersecurity responsibilities,
- the overall and cybersecurity-specific suppliers and partners,
- cybersecurity operations and their alignment with overall operations,
- cybersecurity risks in the context of broader enterprise risks, and
- results related to each of these areas.
The questions in the BCEB lead users to manage all areas affected by cybersecurity in alignment with their organization’s characteristics, environment, and strategy.
Cybersecurity is Everyone’s Job
It is often said that a team is only as strong as its weakest player, and the best defense is a good offense. To manage risks and ensure continuity of operations, it’s imperative that leaders and managers take a direct role in motivating their workforce to remain cyber aware—especially in today’s maximum telework space, where so many remote workers are connecting to network services from outside their organization’s boundaries.
Think of cybersecurity as a team sport, in which all players must make and implement strategic decisions about risks, policies, and operations. To that end, inspired by the Baldrige Cybersecurity Initiative, following are six tips from which every business playbook can benefit to create an environment for success now and in the future.
- Keep your assets up to date and fully patched.
Maintain an inventory of your IT assets, and keep them up to date by patching. Disable unused ports and services. Implement anti-virus/anti-malware/anti-phishing technologies where feasible to prevent, detect, and mitigate malware, including ransomware. - Look comprehensively at your data and consider eliminating or archiving things you no longer need.
If you haven’t used it in years, then it may no longer be a mission-essential function to your business or a vital part of responding to a cybersecurity event. Time is of the essence when a potential incident occurs. Mean time to inventory, detect, and respond (PDF) are just three important metrics that can impact breach costs for your organization. - Put your disaster response plan to the test, and correct any parts of the process that do not go as planned.
Everyone on the team should understand their roles and responsibilities for responding to a cyberattack, have emergency contact information on hand for other team members they need to communicate with, and know what the game plan is before that incident becomes a breach (PDF). - Build in employee cybersecurity awareness continuously through bulletins, text or email alerts, regular training, and other activities.
This will help everyone understand that vulnerabilities arise and pose a threat to the entire organization, not just one person. - Report social engineering incidences to your organization’s security team.
Common examples include email phishing—fraudulent messages containing spam links or attachments. When an email looks suspicious, even if it “appears” to be from someone you know, it’s best to delete it. Remain cognizant of other types of phishing attacks as well, such as vishing (scam phone calls), smishing (fraudulent SMS messages), and angler phishing (fake social media accounts). - Implement multi-factor authentication (MFA).
MFA (PDF) adds an additional layer of security around sites containing sensitive information, or whenever enhanced security is desirable, and makes it more difficult for unauthorized people to log in as the account holder. To further increase account security, ensure that you’re also using strong passwords. NIST’s David Temoshok adds, “Since multiple long passwords are difficult to remember and manage, consider the use of a password manager for stronger, simpler password management.” For additional information on password managers, consult NIST Special Publication 800-63.
Improve Your Organization’s Cybersecurity Risk Management Efforts

Baldrige Cybersecurity Excellence Builder
The Baldrige Cybersecurity Excellence Builder, Version 1.1 is a self-assessment tool to help organizations better understand the effectiveness of their cybersecurity risk management efforts and identify improvement opportunities in the context of their overall organizational performance.





