Improving the Nation's Cybersecurity: NIST’s Responsibilities Under the May 2021 Executive Order
Overview | Completed Assignments | Latest Updates
Overview
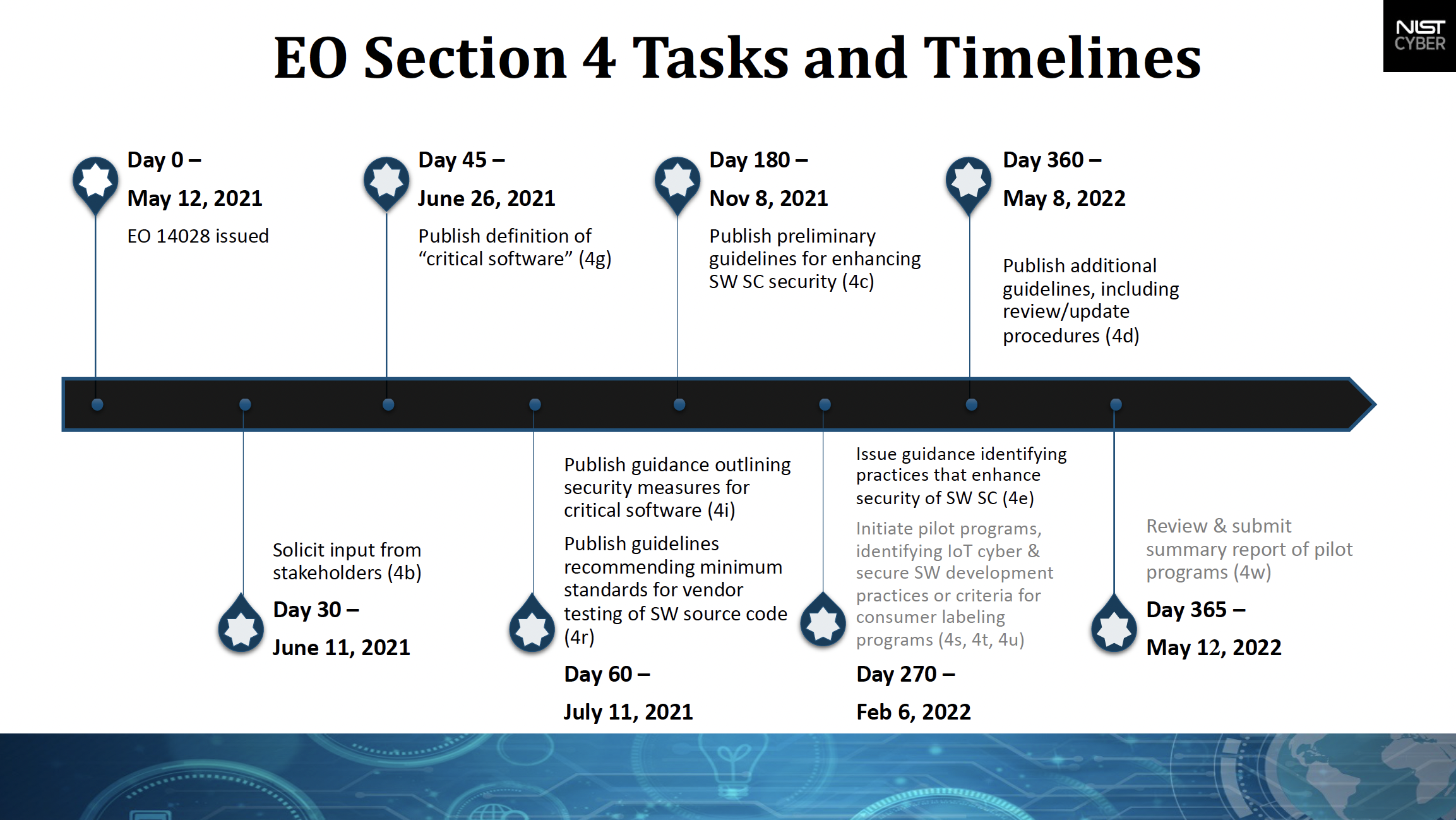
The President’s Executive Order (EO) 14028 on Improving the Nation’s Cybersecurity issued on May 12, 2021, charges multiple agencies – including NIST – with enhancing cybersecurity through a variety of initiatives related to the security and integrity of the software supply chain.
Section 4 directs NIST to solicit input from the private sector, academia, government agencies, and others and to identify existing or develop new standards, tools, best practices, and other guidelines to enhance software supply chain security. Those guidelines, which are ultimately aimed at federal agencies but which also are available for industry and others to use, include:
- criteria to evaluate software security,
- criteria to evaluate the security practices of the developers and suppliers, and
- innovative tools or methods to demonstrate conformance with secure practices.
NIST is to consult with other agencies in producing some of its guidance; in turn, several of those agencies are directed to take steps to ensure that federal procurement of software follows that guidance.
The EO also assigns NIST to work on two labeling efforts related to consumer Internet of Things (IoT) devices and consumer software with the goal of encouraging manufacturers to produce – and purchasers to be informed about– products created with greater consideration of cybersecurity risks and capabilities.
Completed
NIST solicited input from the private sector, academia, government agencies, and others through multiple requests for position papers, comments on drafts, presentations, and discussions at heavily attended virtual workshops, briefings and listening sessions. These engagements informed all of NIST’s actions under Section 4.
NIST consulted with the National Security Agency (NSA), Office of Management and Budget (OMB), Cybersecurity & Infrastructure Security Agency (CISA), and the Director of National Intelligence (DNI) and then defined “critical software” by June 26, 2021.
NIST published guidance outlining security measures for critical software by July 11, 2021, after consulting with CISA and OMB. By that same date, after consulting with the NSA, NIST published guidelines recommending minimum standards for vendors’ testing of their software source code.
NIST issued preliminary guidelines by November 8, 2021, based on stakeholder input and existing documents, for enhancing software supply chain security.
After consulting heads of various agencies by February 6, 2022, NIST issued additional guidance that identifies practices that enhance software supply chain security, with references to standards, procedures, and criteria.
Regarding cybersecurity labeling for consumers, by February 6, 2022, NIST identified:
- IoT cybersecurity criteria for a consumer labeling program and
- Secure software development criteria for a consumer software labeling program.
NIST issued additional information about its software supply chain guidance plans, including review and update procedures, by May 8, 2022.
The Secretary of Commerce, in consultation with the heads of other agencies, provided to the President, through the Assistant to the President for National Security Affairs (APNSA), a report that reviews the progress made under this section and outlines additional steps needed to secure the software supply chain.
NIST conducted a review of the pilot programs for cybersecurity labeling of consumer IoT products and consumer software products, consulting with the private sector and relevant agencies to assess the effectiveness of the programs, determining what improvements can be made going forward, and submitted a summary report on May 10, 2022, to the Assistant to the President for National Security Affairs (APNSA).
Latest Updates
NIST releases summary report on Progress Implementing Section 4 of Executive Order 14028 (July 11, 2022)
NIST releases summary report on the labeling initiatives under the EO (May 24, 2022)
New EO Guidance for Cybersecurity Supply Chain Risk Management (May 5, 2022)
NIST Issues Guidance on Software, IoT Security and Labeling (February 4, 2022)
2nd Public Draft SP 800-161 Revision 1 Workshop (December 1, 2021)
Executive Order 14028: Guidelines for Enhancing Software Supply Chain Security (November 8, 2021)