Software Security in Supply Chains: Guidance, Purpose, Scope, and Audience
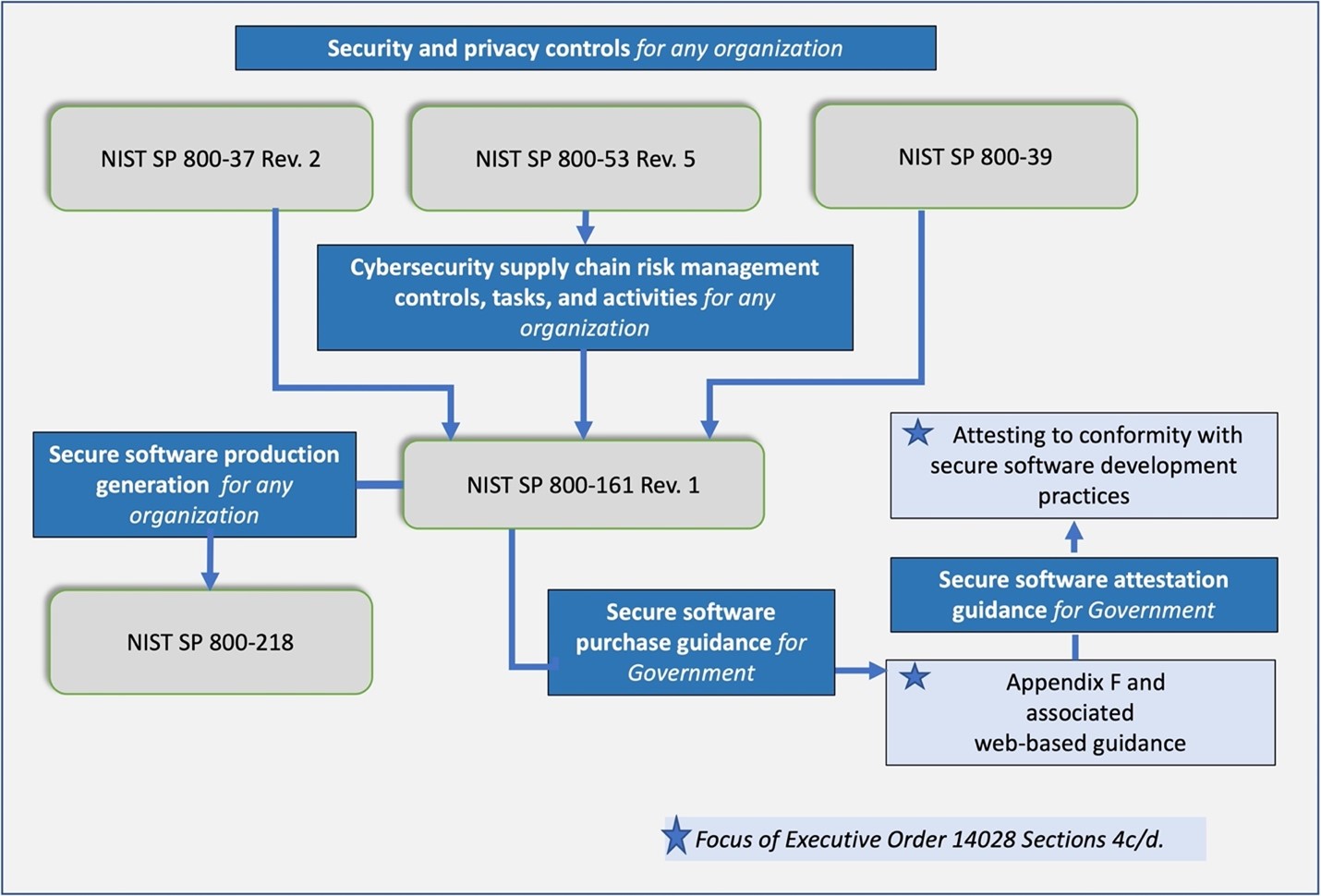
This guidance informs the acquisition, use, and maintenance of third-party software and services for agencies’ information technology (IT), Cybersecurity Supply Chain Risk Management (C-SCRM) Program Management Office, acquisition/procurement, and other functions in response to Section 4(c) and 4(d) of EO 14028. It calls for applying the controls in SP 800-161r1upd1 to suppliers and — where feasible — adopting new software supply chain security recommendations.
The impact of Section 4(c) and 4(d) directives will continue to evolve through 2022 and beyond. The concepts introduced here will similarly evolve. NIST will maintain this guidance in accordance with Section 4(d).
This guidance does not include contractual language for federal agencies or cybersecurity concepts and disciplines beyond core software supply chain security use cases.
The primary audience for this guidance are federal agencies that acquire, deploy, use, and manage software from open-source projects, third-party suppliers, developers, system integrators, external system service providers, and other information and communications technology (ICT)/operational technology (OT)-related service providers that must comply with Section 4(d) of EO 14028. As outlined in Fig. 1, Section 4(e) and the associated SP 800-218 contain guidance on secure software produced or developed in-house by federal agencies or by third-party suppliers.
Content:
- Introduction
- Guidance, Purpose, Scope, and Audience
- EO-Critical Software and Security Measures for EO-Critical Software
- Software Cybersecurity for Producers and Users
- Software Verification
- Evolving Standards, Tools, and Recommended Practices
- Additional Existing Industry Standards, Tools, and Recommended Practices
- Frequently Asked Questions (FAQs)

