NICE Framework Success Story: Cybersecurity Curricula
By Morgan State University
Use: Create Learning Outcomes
ORGANIZATIONAL PROFILE
Morgan State University is the premier public urban research university in Maryland, known for its excellence in teaching, intensive research, effective public service and community engagement. Morgan prepares diverse and competitive graduates for success in a global, interdependent society.
The National Security Agency (NSA) and the U.S. Department of Homeland Security (DHS) have designated Morgan State University as a National Center of Academic Excellence in Cyber Defense Education (CAE-CD).
Cybersecurity courses at Morgan have been mapped to the CAE Knowledge Units and NICE Framework with the help of a cybersecurity curriculum development tool developed by funding from NSA. Cybersecurity education at Morgan covers a variety of areas in computer science, computer engineering, and information systems. Morgan Computer Science provides a solid foundation in theoretical computer science as well as applied approached in cybersecurity, software engineering, artificial intelligence/data science, and robotics.
DRIVERS
- Gaps between cybersecurity learning and workforce development.
- Lack of hands-on skills.
- The need of a pipeline of students to study cybersecurity, for internships, and to work for cybersecurity companies.
- Alignment of learning with CAE designation and industry needs.
- Demonstration of artificial intelligence (AI)-enabled cybersecurity curriculum development tool.
- Preparation of next-generation cybersecurity warriors to take on the challenges and threats in cyberspace.
PROCESS
Course Development: Top Down and Bottom Up
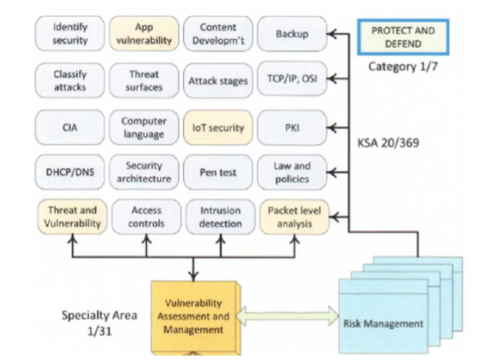
Course development using the NICE Framework was approached from both the top-down and bottom-up. For cybersecurity class COSC 351, we went top-down, working from Specialty Area to Knowledge, Skills, and Abilities (KSAs), and then mapped to the Vulnerability Assessment Analyst Work Role. Later, the AI tool reminded us to add pen test in order to obtain a strong “mapping”.
For our quantum computing/crypto class COSC 386/486/586, we used the bottom-up approach. First, we followed the NICE Framework and identified Knowledge of cryptography and cryptographic key management concepts (K0019). Then we found 8 Work Roles associated with K0019, from which we selected four. We added quantum key distribution as an additional requirement and plan to gather experiences to forward to the NICE program office for future expansion and revisions.
TIE-IN WITH THE NICE FRAMEWORK
Designing a workforce-oriented cybersecurity curriculum or training is vital in academia as well as in private sector and government. A database built on the NICE Framework enables people to search Knowledge, Skills, and Abilities (KSAs) and Work Roles on a dynamic website. Furthermore, it allows the use of AI in assisting curriculum development, guaranteeing incorporation of the most pertinent KSAs. Educators can also search by Work Roles to prepare students for roles pecific skills sought by industry.
BENEFITS & IMPACT
“Use of the NICE Framework prepares students with the KSAs that shorten the transition from study to work.”
–Paul Wang, Chair and Professor of Computer Science, Morgan State University
The successful implementation of the NICE Framework has enhanced the cybersecurity education and research in areas such as curriculum development, computer architecture and security, IoT/CPS security, and quantum cryptography and cryptologic study. The research in return reshapes cybersecurity learning to be more hands-on and workforce oriented.
For the NICE Framework database project, the team has shared the database with private sector including Coca-Cola, TSYS, and a number of universities. The NICE Framework based AI-assist cybersecurity curriculum/training tool has been published by NSA and shared with academia, industry, and government in the nation.
CONTACT INFORMATION & RESOURCES
Contact:
Paul Wang
Chair and Professor of Computer Science, Morgan State University
shuangbao.wang [at] morgan.edu (shuangbao[dot]wang[at]morgan[dot]edu)
Websites:
Morgan Computer Science
https://www.morgan.edu/computerscience
Morgan State University
https://www.morgan.edu/
National Centers of Academic Excellence:
https://niccs.cisa.gov/formal-education/national-centers-academic-excellence-cae

